How Crypto Gets Hacked: Issue #3
Bitfinex Hackers Caught, Wormhole Part 2, & FDIC Crypto Regulation
Disclaimer: I’ll be talking about individual crypto projects in this series but this is for informational purposes only and not a solicitation to buy or sell any cryptoassets.
Do your own due diligence.
🎉 GOT EM! 🎉
If you were on social media this week, it was impossible not to see or hear all the news floating around of Ilya Lichtenstein and Heather Morgan after they were charged with conspiracy to launder $4.5 billion in bitcoin, which they had stolen in the famous 2016 hack on Bitfinex.
Here are some favorites:





Bitfinex was the largest dollar-based bitcoin exchange in 2016, so the hack was very significant at the time. Along with Mt. Gox, it haunted the industry and proved to everyone that they needed to maintain custody over their own crypto and not leave it on exchanges (hence “not your keys, not your coin”).
In April 2021, as the price of bitcoin was reaching new highs, the hackers tried to move $750 million worth of bitcoin for some unknown reason, and this may have been what set off alarm bells to the DOJ that they were trying to launder their stolen bitcoin.
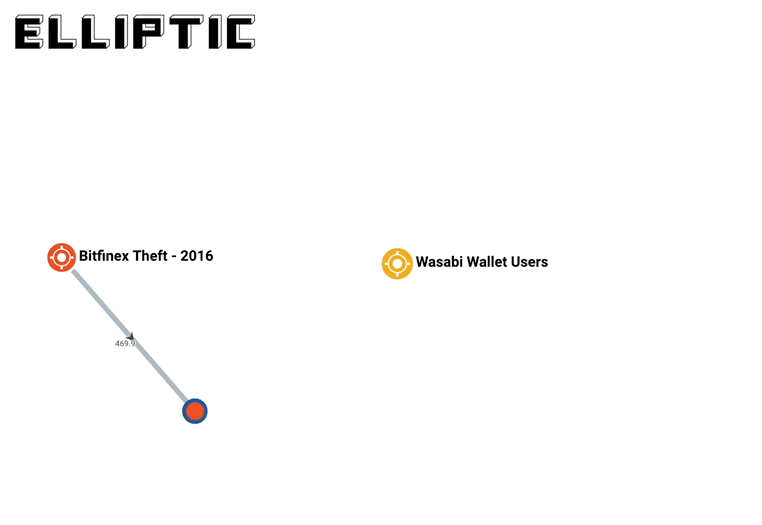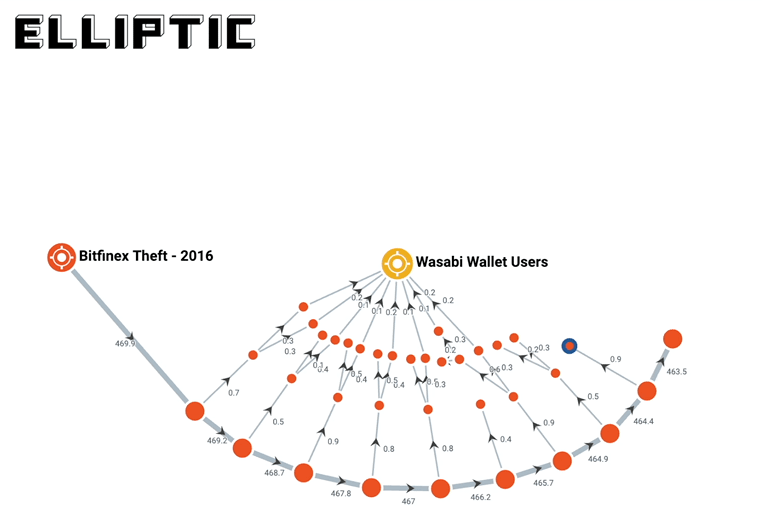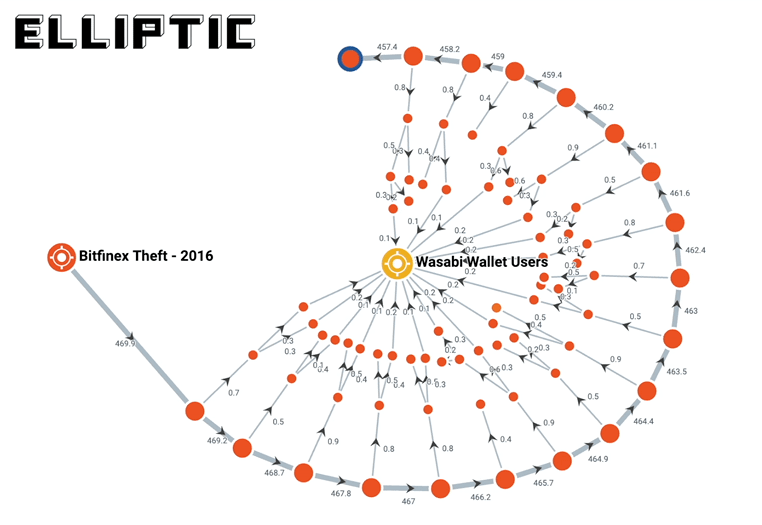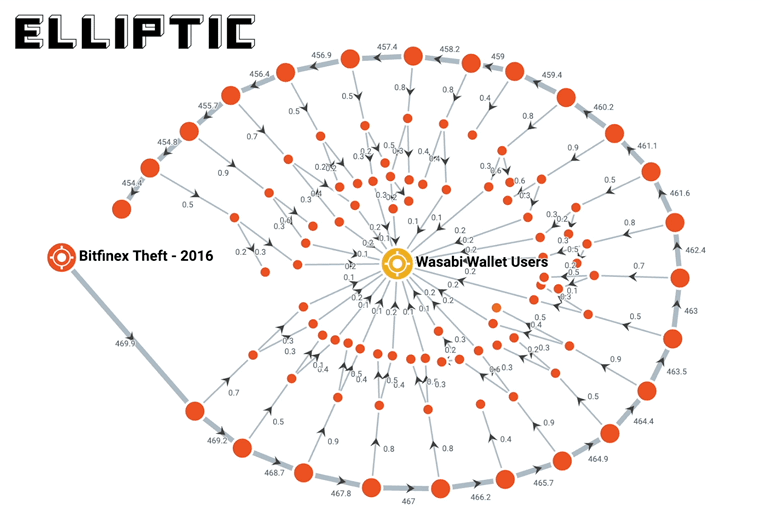
A month later, blockchain forensics and compliance firm Elliptic found out what they were doing: they were slowly laundering the bitcoin through the darknet and private wallets:
Elliptic’s analysis of blockchain transactions relating to the bitcoins stolen from Bitfinex, shows that the majority are still held in private wallets. They are in the process of being transferred to a range of third-party services to be laundered or cashed-out, but slowly and in small increments. This is illustrated below, where we use our investigations software Elliptic Forensics to trace one outflow from the thief’s wallet, over the course of a number of days and through various wallets, all the way to its ultimate destination (more on Wasabi later).
You can read more about it in the link above. It goes really in depth into what darknet sites were used, how they used privacy wallets that use “CoinJoin” techniques to obfuscate tracing on the blockchain (similar to mixers), and how they used less-regulated exchanges all to try to launder the stolen bitcoin and cash out.
The DOJ did not say how they did it, but they were able to decrypt a digital wallet stored on a cloud server which was owned by Lichtenstein. This is how they were able to seize a majority of the stolen bitcoin:
According to court documents, Lichtenstein and Morgan allegedly conspired to launder the proceeds of 119,754 bitcoin that were stolen from Bitfinex’s platform after a hacker breached Bitfinex’s systems and initiated more than 2,000 unauthorized transactions. Those unauthorized transactions sent the stolen bitcoin to a digital wallet under Lichtenstein’s control. Over the last five years, approximately 25,000 of those stolen bitcoin were transferred out of Lichtenstein’s wallet via a complicated money laundering process that ended with some of the stolen funds being deposited into financial accounts controlled by Lichtenstein and Morgan. The remainder of the stolen funds, comprising more than 94,000 bitcoin, remained in the wallet used to receive and store the illegal proceeds from the hack. After the execution of court-authorized search warrants of online accounts controlled by Lichtenstein and Morgan, special agents obtained access to files within an online account controlled by Lichtenstein. Those files contained the private keys required to access the digital wallet that directly received the funds stolen from Bitfinex, and allowed special agents to lawfully seize and recover more than 94,000 bitcoin that had been stolen from Bitfinex. The recovered bitcoin was valued at over $3.6 billion at the time of seizure.
Once again, the permanent traceability of the blockchain helped law enforcement identify and catch the criminals. This is a win! 🥳
Wormhole Hack, Part 2
In Issue #1, I discussed the recent Wormhole exploit. Now Chainalysis has brought to light some of the serious issues with making blockchains interoperable.
Wormhole was used to allow users to move assets like cryptocurrencies and NFT’s across the Solana and Ethereum blockchains. Normally if a person wanted to use ETH on the Solana blockchain, they would deposit ETH into Wormhole and receive weETH, a “wrapped” version of the ETH that was usable in the Solana blockchain ecosystem.
The reason this hack added risk to the entire ecosystem is that 120K wrapped ETH was created out of thin air, and was therefore unbacked. Without any ETH backing up weETH, people would lose confidence they would be able to redeem their weETH for ETH again, and this is the type of situation that could have created a bank run.
But as I stated in Issue #1, JumpCrypto, Wormhole’s parent company, jumped in to replace the ETH that was stolen and prevent a bank run from happening. Much like JP Morgan and JD Rockefeller restoring confidence in the banking system during the Panic of 1907, crypto sometimes needs to get bailed out by wealthy benefactors when they get themselves in trouble.
The good news is in the aftermath of this hack, investigators are closely following the addresses of the hacker and will know if he/she ever moves the funds.
From Chainalysis:
DeFi protocols and cross chain bridges are now critical infrastructure in the cryptocurrency ecosystem and any successful attack has cascading effects. If users can bridge funds across chains, it means each chain’s assets are only as secure as the other chains they connect to, along with the protocols built on top of those chains. If users think their assets could be unbacked after a hack, we could see something akin to a bank run, creating major price declines and possibly causing protocols to become insolvent, all of which could affect the other interconnected protocols.
While not foolproof, a valuable first step towards addressing issues like this could be for extremely rigorous code audits to become the gold standard, both for those building protocols and for the investors evaluating them. And over time, the strongest, safest smart contracts can serve as templates for developers to build from, such as those offered by the Open Zeppelin Project.
This was the first time I’ve heard of Open Zeppelin, a GitHub repository of community-vetted Ethereum code that anyone can use to build new crypto projects. I think it’s a great idea, and hope it helps prevent further exploits in the future.
FDIC on the Risks of Crypto-Assets
USA’s acting chairman Martin J. Gruenberg recently announced the FDIC’s priorities for 2022, which included making sure crypto-assets did not pose a risk to the US federal banking system.
From the press release:
Evaluate Crypto-Asset Risks: The rapid introduction of a variety of crypto-asset or digital asset products into the financial system could pose significant safety and soundness and financial system risks. It is imperative that the federal banking agencies carefully consider the risks posed by these products and determine the extent to which banking organizations can safely engage in crypto-asset-related activities. To the extent such activities can be conducted in a safe and sound manner, the agencies will need to provide robust guidance to the banking industry on the management of prudential and consumer protection risks raised by crypto-asset activities.
From an earlier press release in November 2021, it lays out their potential game plan for cryptoassets in a little more detail:
Throughout 2022, the agencies plan to provide greater clarity on whether certain activities related to crypto-assets conducted by banking organizations are legally permissible, and expectations for safety and soundness, consumer protection, and compliance with existing laws and regulations related to:
Crypto-asset safekeeping and traditional custody services.
Ancillary custody services.
Facilitation of customer purchases and sales of crypto-assets.
Loans collateralized by crypto-assets.
Issuance and distribution of stablecoins.
Activities involving the holding of crypto-assets on balance sheet.
The agencies also will evaluate the application of bank capital and liquidity standards to cryptoassets for activities involving U.S. banking organizations and will continue to engage with the Basel Committee on Banking Supervision on its consultative process in this area. The agencies continue to monitor developments in crypto-assets and may address other issues as the market evolves. Further, the agencies will continue to engage and collaborate with other relevant authorities, as appropriate, on issues arising from activities involving crypto-assets.
The good news here for all the crypto-evangelists and crypto-curious is that the FDIC is looking for ways to integrate stablecoins and crypto-based collateral into the existing system, which I think could be a good thing in the long run for both the existing banking system and crypto.
The bad news for some of them: thinking the ecosystem would remain regulation-free forever is a pipe dream. Regulation is coming to crypto whether you want it to or not, the important thing is to work together and come up with solutions that work for everyone (much like the Anchorage protocol is doing).
Thanks for reading, and have a great weekend!
PS:
Unchained had an interview with the cofounder of Elliptic to talk about the Bitfinex hack and how law enforcement may have caught them on her podcast, and you can listen to that here: